SonicWALL Threat Research Labs recently received reports of attackers targeting websites with ransomware.
Attackers are uploading malicious PHP files onto the websites. These PHP files allow the attacker to encrypt the website’s files and then extort money from the site’s owner. Once uploaded, the attacker then connects to the ransomware via a web browser, as follows:
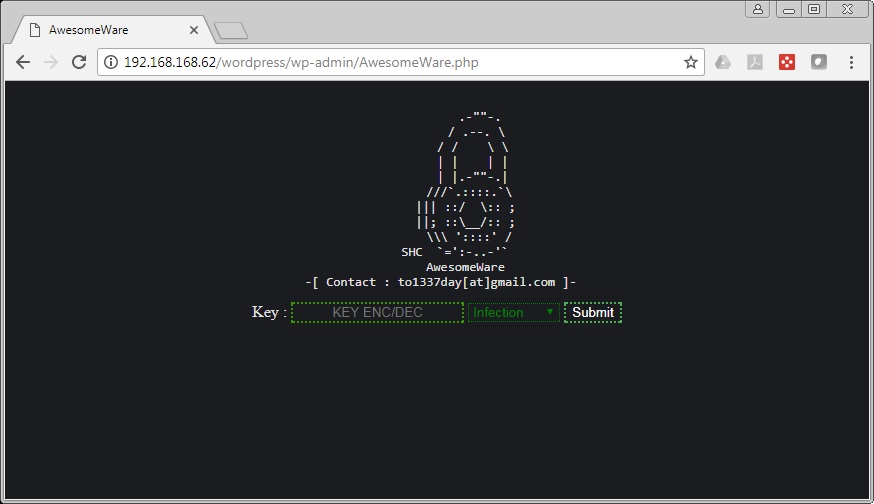
The attacker can then submit a complex encryption key to encrypt the site’s content.The malware overwrites the .htaccess file.
This redirects the website to the file shor7cut.php.
In addition, the ransomware traverses the directory searching for files to encrypt. The file contents are then encrypted using PHP’s mcrypt function, then it is renamed with the .shor7cut extension name.
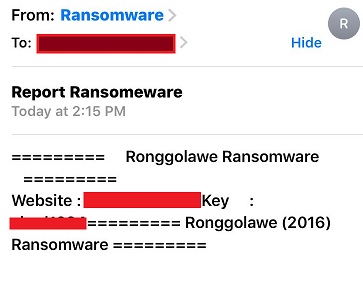
Once the malware is done encrypting, it sends an email to the attacker containing the encryption key:
Once the site owner pays the ransom, the attacker then goes back to the ransomware PHP and choose the “DeInfection” option:
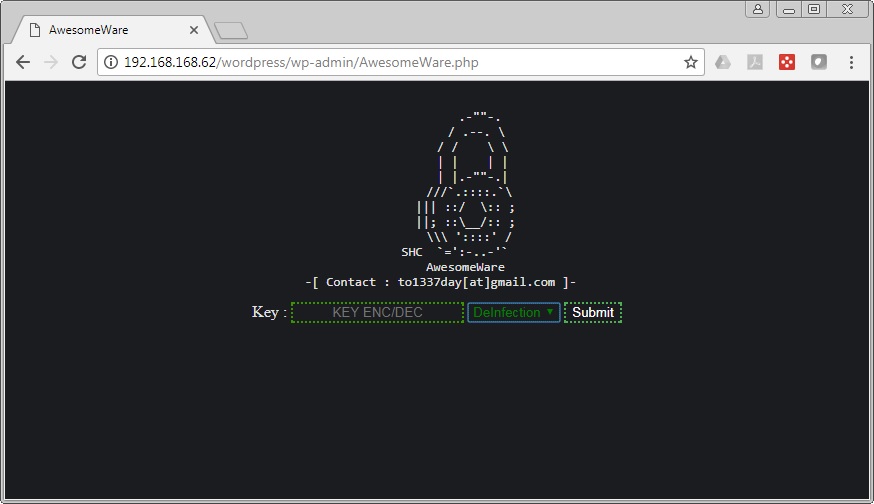
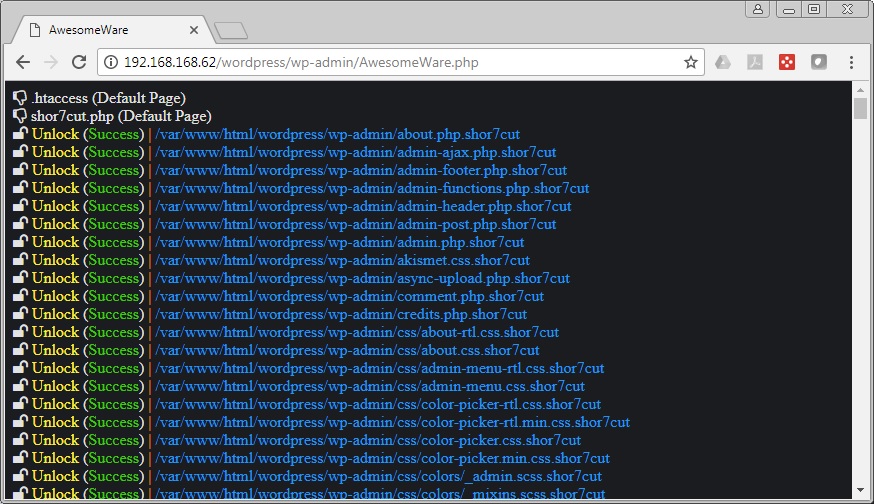
Entering the appropriate key, the ransomware then restores the files.
SonicWALL Threat Research Team has the following signature to protect their customers from this type of attack:
- GAV 17970: Ronggolawe.RSM
- WAF 1669: Ronggolawe.RSM

